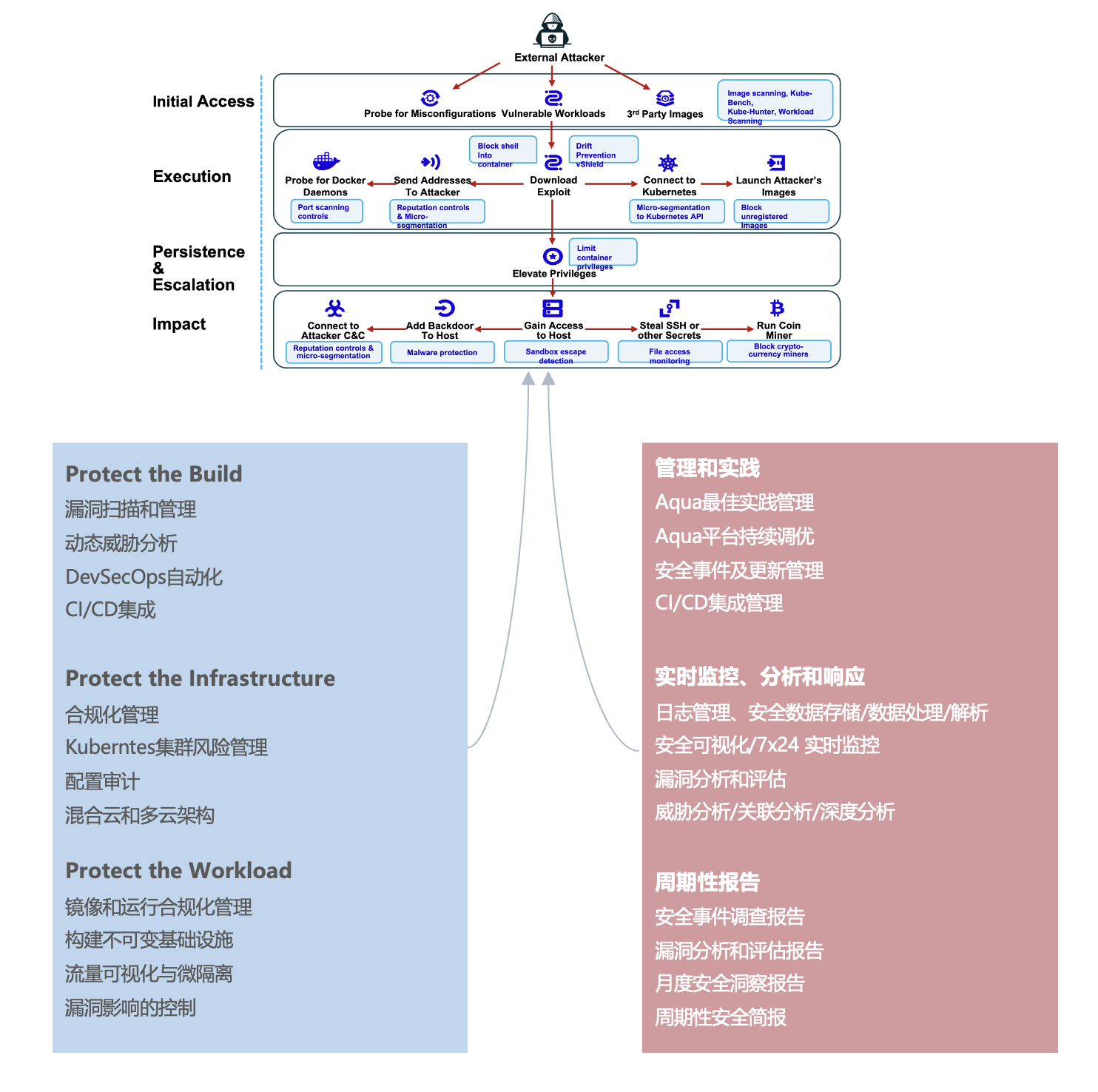
Cloud Native Security Issues
In recent years, as cloud-native technology is becoming more and more popular, cloud-native security is also gaining widespread attention and importance. The security of cloud-native environment infrastructure, container image security, workload operation security, and the security of the entire cloud-native ecology are issues that need to be addressed.
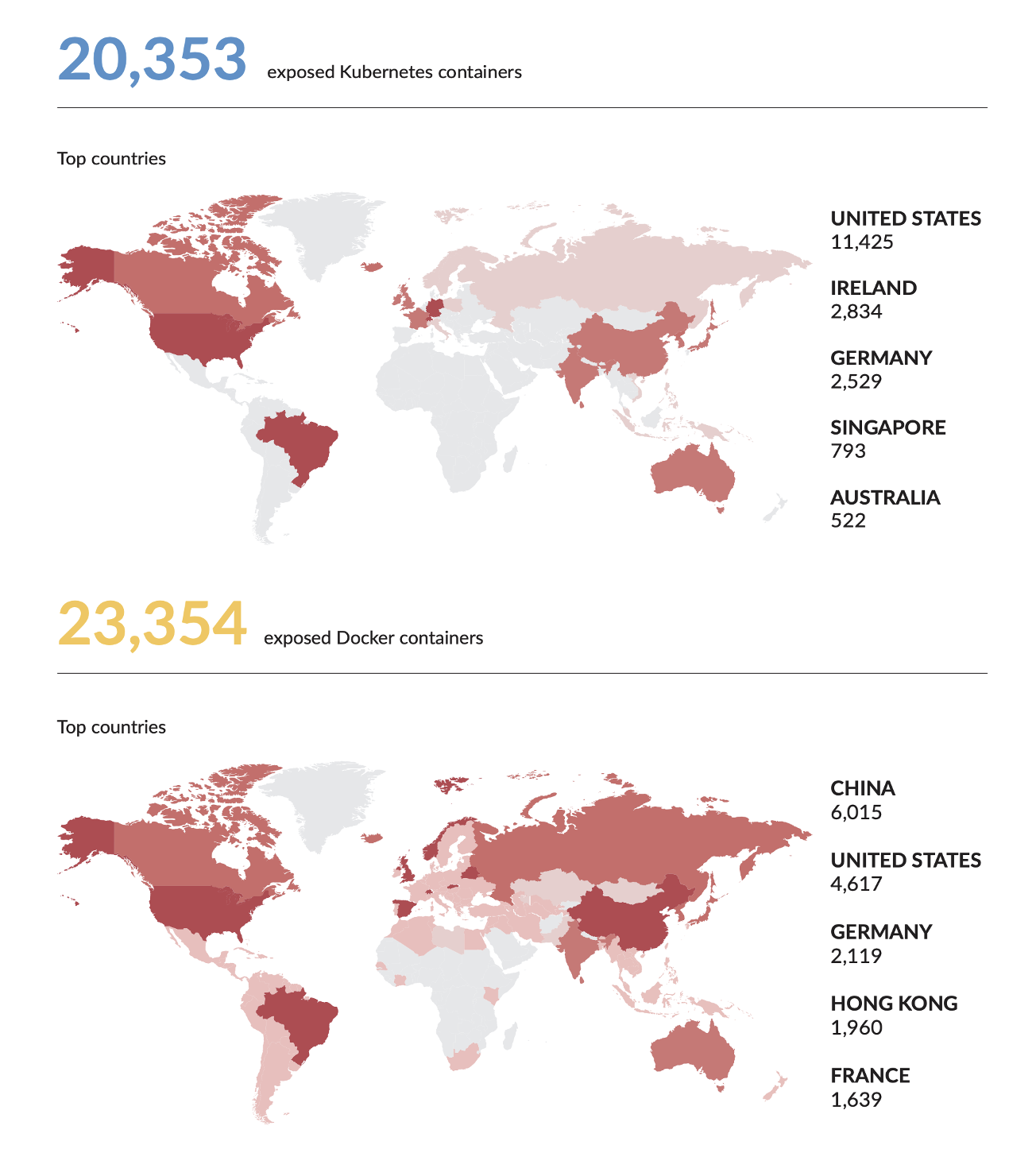
- Large number of unprotected exposed containers/Pods
- Potential security risks due to incorrect cluster security settings
- New fileless attacks, escapes to static security checks
- Container escapes due to container engine vulnerabilities
- Blurred container east-west boundaries and lack of isolation means
- Massive non-compliant use of “rich” containers
Managed Cloud Native Security
Cloudfall MCNS service provides comprehensive security hosting for enterprise cloud-native environments. We focus on the security of the complete DevOps lifecycle, including development, build, infrastructure and operation phases, and use leading international cloud-native security management tools to help users improve security in the DevOps process.
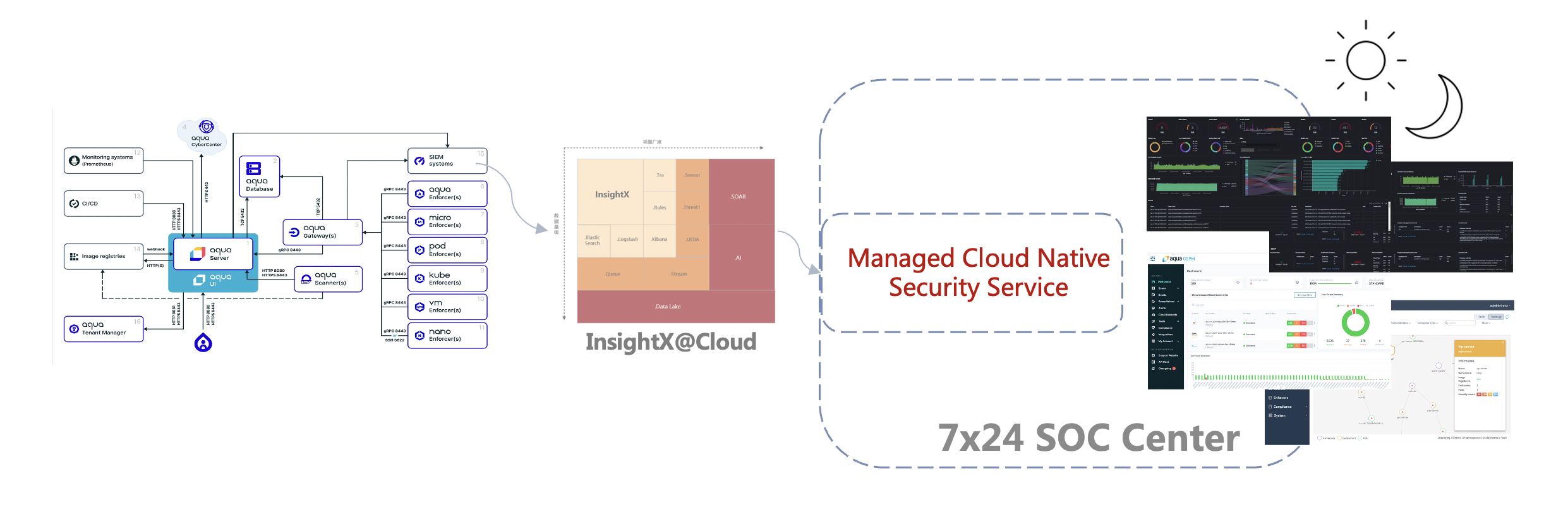
Cloudfall MCNS service supports containers, K8s system detection and assessment, CI/CD, compliance, operational state detection and more, and helps set security compliance baselines and best practice see standards to secure enterprise compliance. Meanwhile, thanks to the access to IX platform and real-time monitoring and analysis by 7X24 security operations team, in-depth analysis of continuous cloud-native environment security can be performed.
Protect the Build
With tools for security “left shifting” (moving checks and verifications early in the development cycle), security testing during the development phase provides users with quick feedback on code and configurations that may be checked later, either manually or automatically, and can reduce the friction of introducing more secure practices.
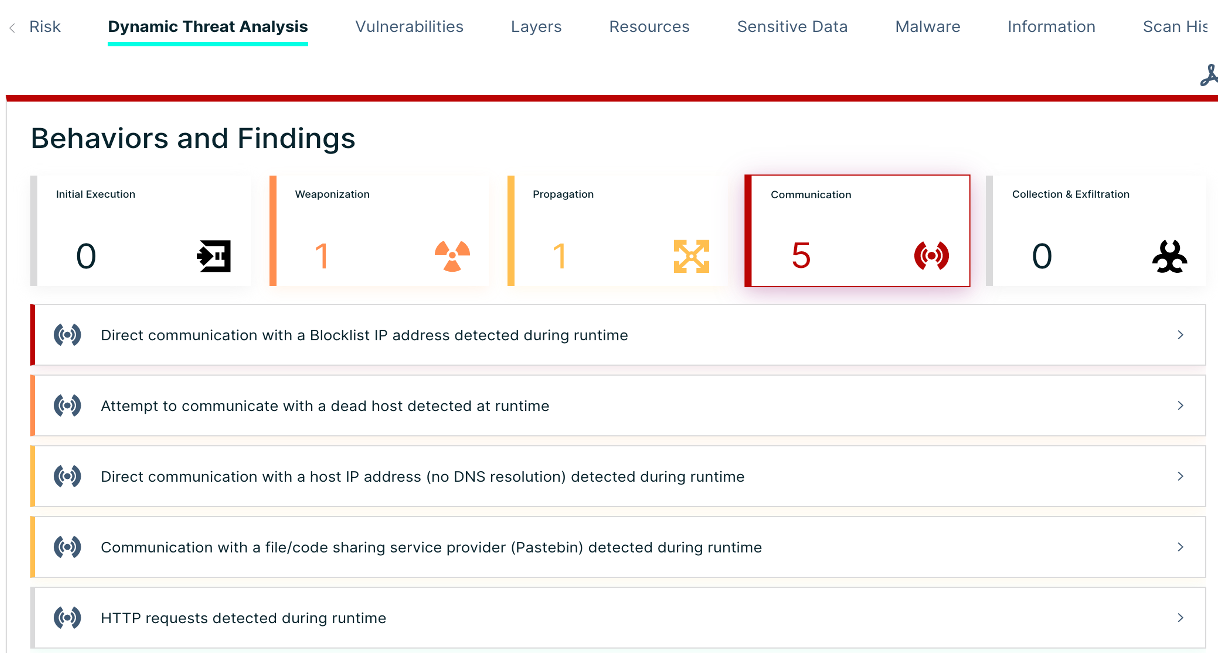
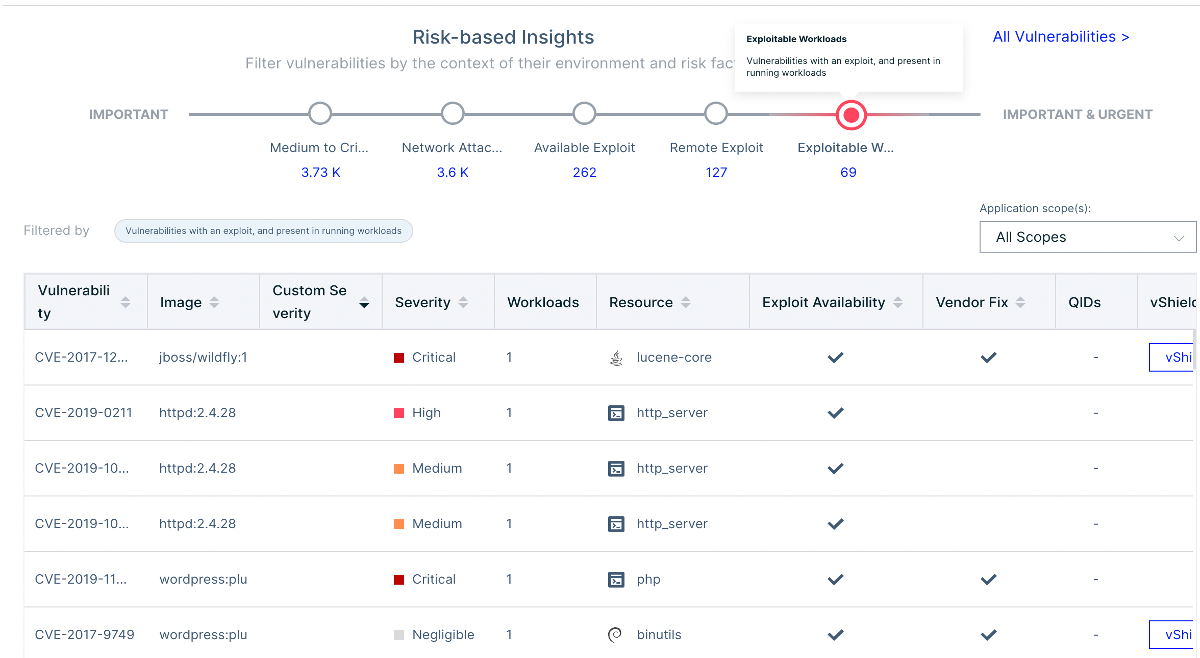
During the build phase, Cloudfall Container Security Services provides capabilities such as unknown threat detection, vulnerability shadow line assessment, CI/CD integration, etc. We help users prioritize all scanned vulnerabilities and give them a risk score from CVE, a risk score based on the nature of the vulnerability and how the application is deployed and running, adjusting the priority based on the customer’s specific environment and focusing on remediation for the most important risks.
Protect the Infrastructure
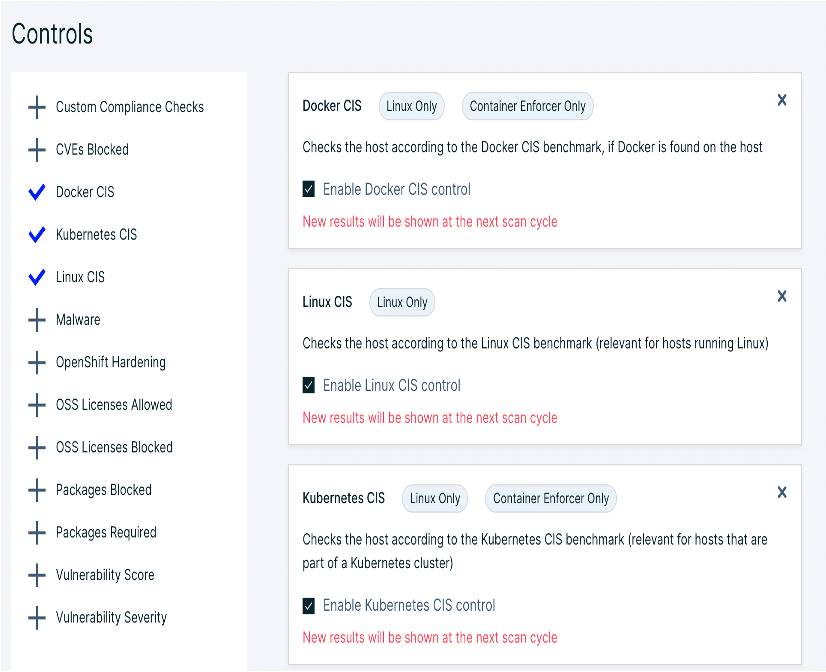
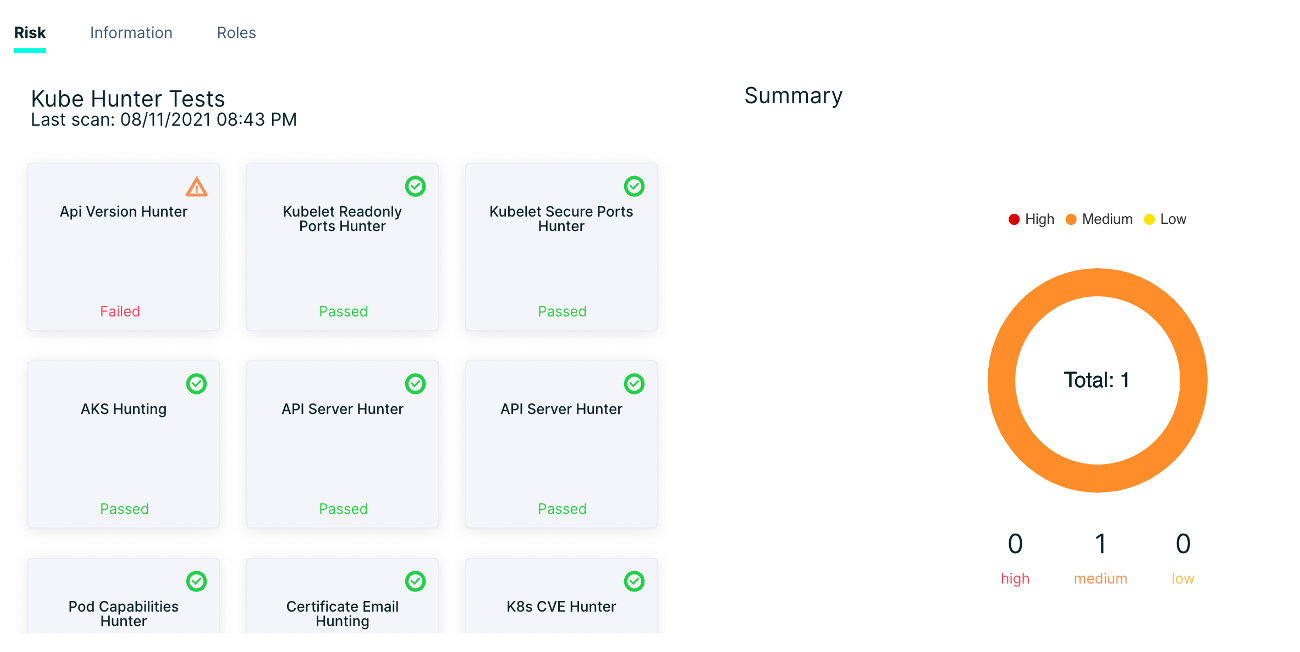
In infrastructure protection, we provide comprehensive compliance management capabilities, Kuberntes cluster risk, KSPM configuration audit, host vulnerability risk, and other capabilities; and through our real-time monitoring platform and service monitoring and management baselines, we identify and alert risks in a timely manner, and help users analyze and improve.
Scanning, monitoring and remediating configuration issues in public cloud accounts across AWS, Azure and other public clouds based on best practices and compliance standards, and implementing compliance controls for PCI, HIPAA, GDPR, etc. across the cloud-native application lifecycle.;
Control the complexity of Kubernetes security with KSPM (Kubernetes Security State Management) and advanced Kubernetes runtime protection. Leverage Kubernetes native capabilities to achieve policy-driven, full lifecycle protection and compliance for your K8s applications
Protect the Workload
The Cloud Workload Protection Platform (CWPP) is now part of the emerging Cloud Native Application Protection Platform (CNAPP) category, designed to protect different types of cloud workloads – such as virtual machines, containers, and serverless functions – deployed in public, hybrid, or multi-cloud environments. Cloudfall uses the industry’s most advanced container security solutions to protect container-based cloud-native applications from development to production, helping users build secure workload environments with technologies and services such as CI scanning, dynamic analysis, risk identification, vulnerability protection, runtime policies, behavioral profiles, workload firewalls, auditing and forensics, and more.
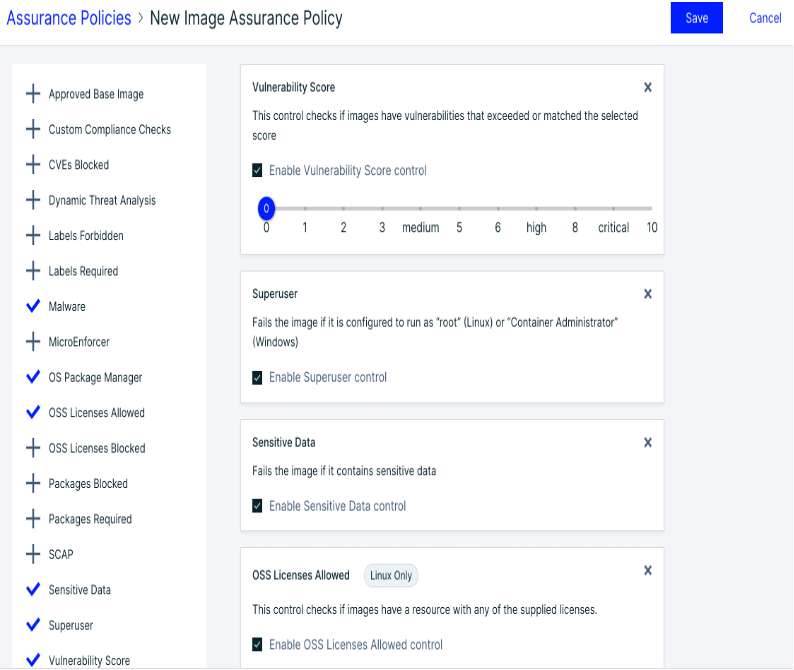
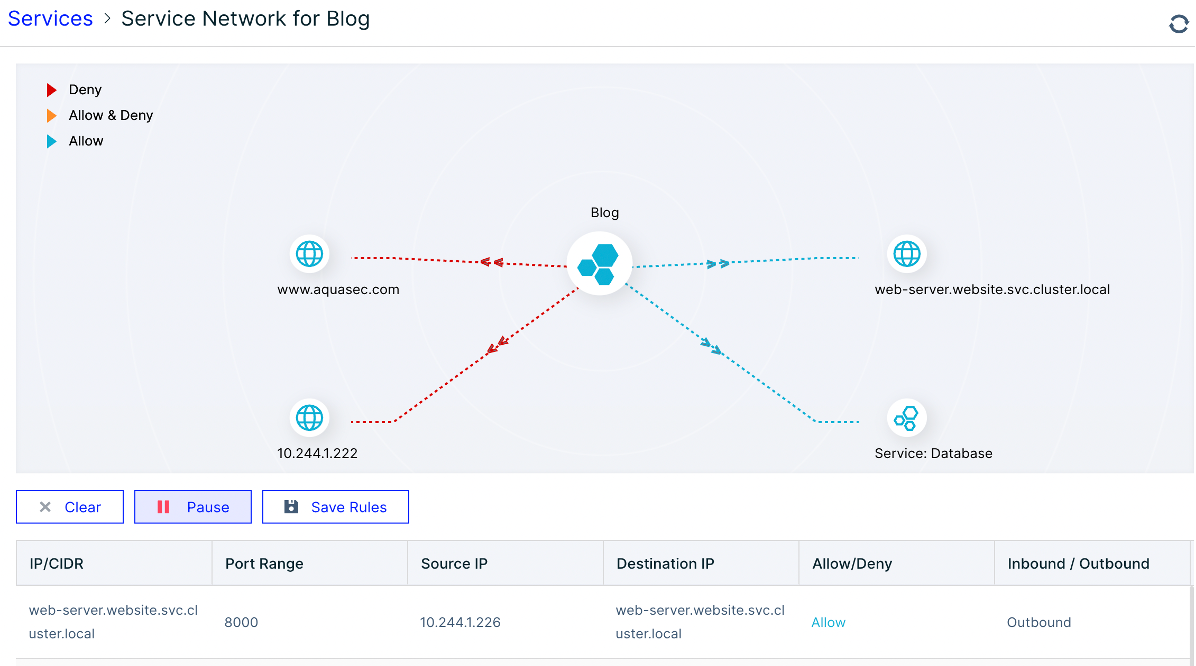
Cloudfall security team can help customers establish and monitor proper access control measures, while providing enterprise-class file integrity monitoring, host auditing and log analysis capabilities that can centrally monitor sensitive events in containers (e.g. sshd, sudo, etc.) and present and analyze them in real-time via the IX platform. At the same time, we can integrate native plug-ins and scanners into any CI/CD tool or workflow to provide vulnerability and compliance scanning results directly to developers.