Cloudfall Threat Analysis Subscription Service
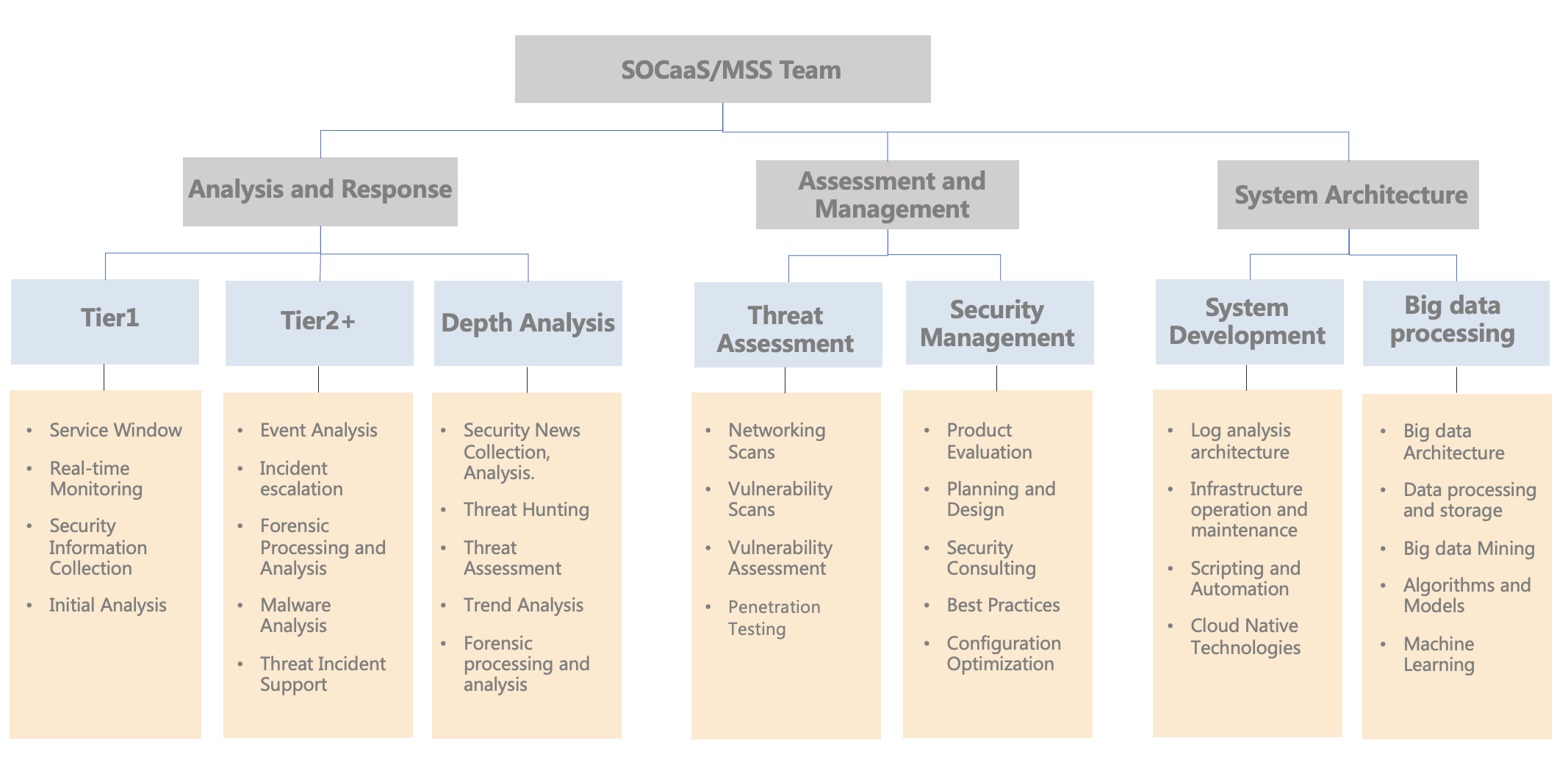
It consists of security analysts with different capabilities using a variety of analytical tools and capabilities; in which a large number of security logs are input, sliced, filtered, aggregated and visualized, combined with our experienced security analysis team, ultimately helping users to clearly locate threats, reduce risks and improve overall security standards.
The real value of threat analysis
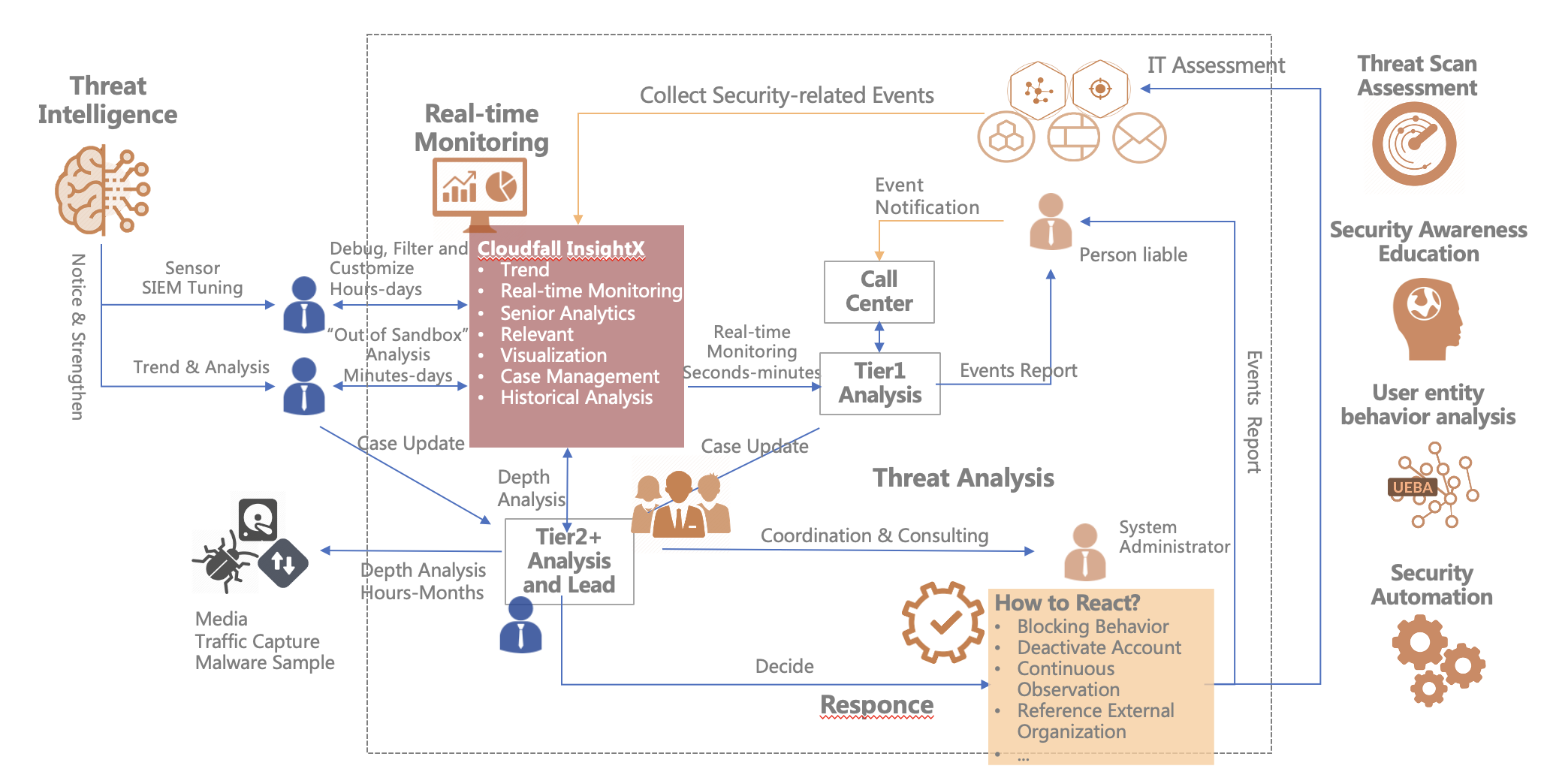
it allows you to find the “signal in the noise”. Key indicators of harm can be found in user activity, system events, firewall acceptance/denial, etc.
Focus on different incident levels
At the same time, with very limited resources to protect assets from attacks; it is also essential to focus on the extent to which different incident levels impact business operations.
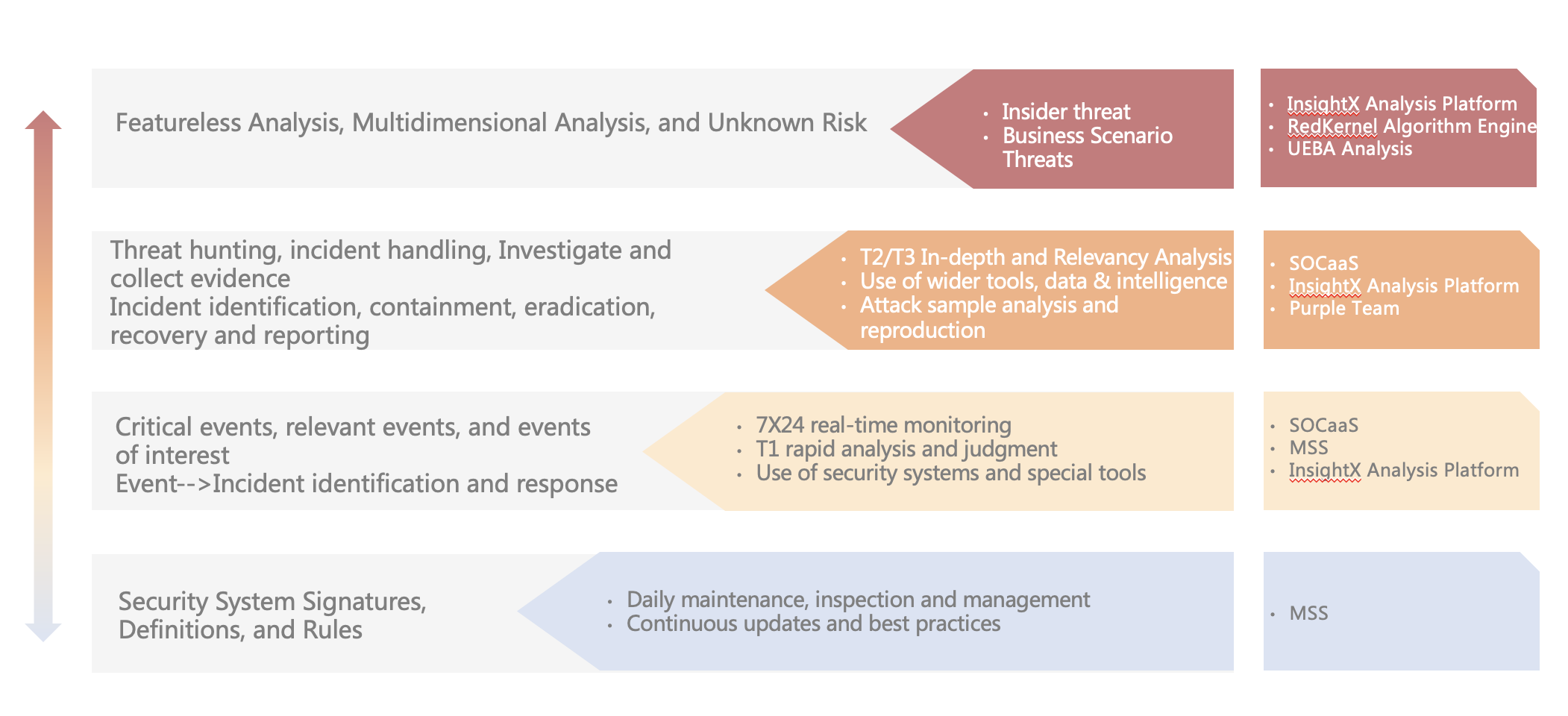
Analysis capabilities are upgrading
As enterprise security environments and postures become more complex, threat analysis capabilities are evolving and upgrading.
Team of Experts
For some of the more complex environments and threat information, there is no substitute for the collective wisdom and experience of the analytics team. Our team of experts has accumulated a wealth of knowledge and experience in endpoint,
network and cloud security, which, combined with our technology platform and analytics tools, can help you focus and solve problems quickly.
This is one of the things we do best
The threat analysis capability itself is a concentration of “people”, “technology” and “process” within the Security Operations Center; it helps locate real security threats by understanding the target audience, using various analysis tools and techniques, and following a process that can be continuously optimized.
Machine Learning
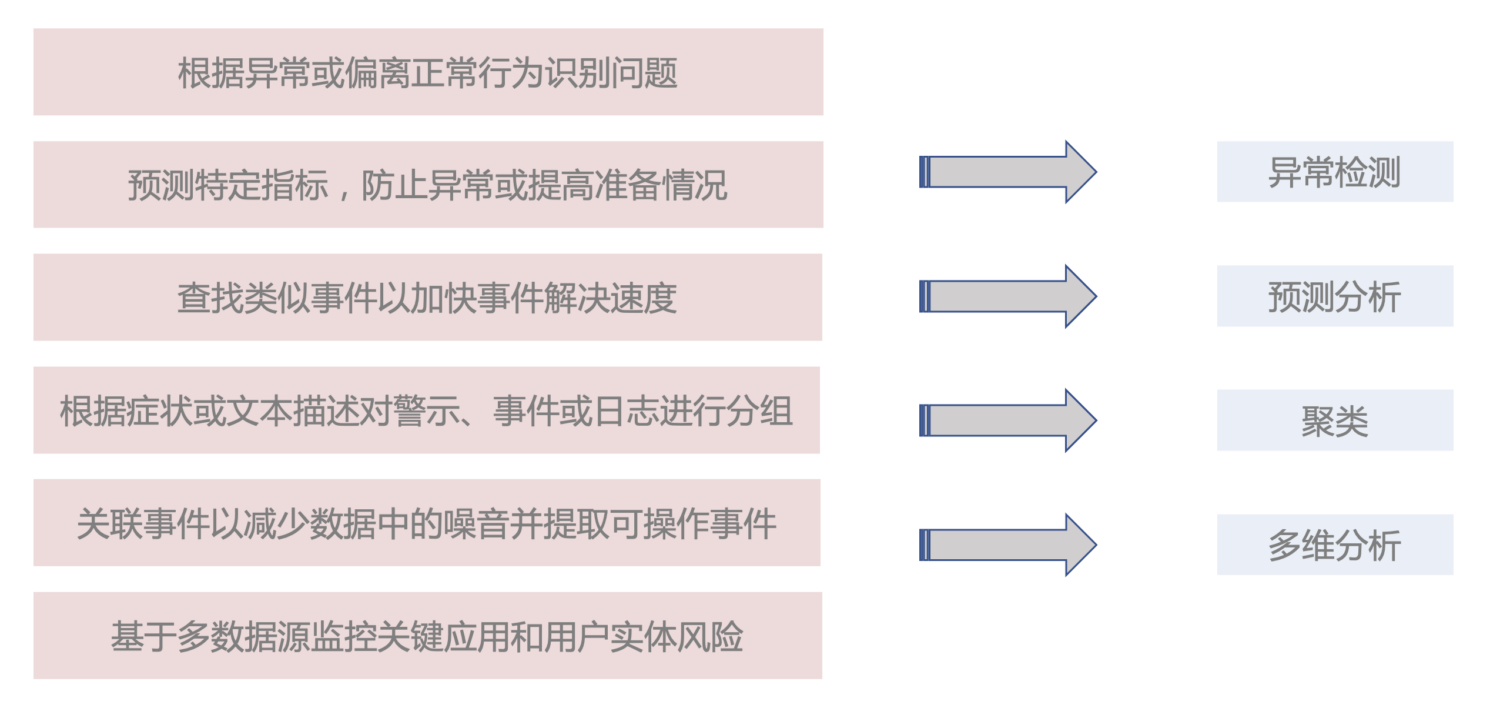
Intricate, rapidly changing security logs make it nearly impossible to detect infrastructure problems, security issues or business problems. In principle, machine learning can help organizations better analyze threats and react to attacks and security incidents. It can also help automate the more trivial tasks previously performed by less skilled security teams.
Resilient machine learning capabilities automatically simulate the behavior of data in real time – trends, periodicity, etc. – to identify problems faster, simplify root cause analysis and reduce false positives.
Our RedKernel machine learning engine is equipped with data processing, data training, feature engineering, and anomaly detection models, combined with the analytical capabilities of security analysts and algorithm engineers to help us focus on unknown risks and anomalous behavior of user entities.