
Numbers
91% of all data breaches start with phishing
the average time to discover a data breach was 146 days
The average time to process a data breach is 84 days
The average loss to a global enterprise from a data breach is $4,000,000.
As we rely more and more on technology to combat today’s evolving cyber threats, the most important factor – people – is easily overlooked. Phishing attacks target people, that is, corporate employees, and 92% of those working in the information industry use email. The attacker is looking for those who are most likely to be trapped. And our products focus on people as the last line of defense, and help enterprises and organizations train internal personnel with targeted security awareness through drill simulation. —— Guard the last line of defense
The weakest link is the top priority for security defense
Users remain the easiest target for attackers in most organizations’ cybersecurity defenses, but trained phishing-aware employees can serve as an effective firewall against such threats.
PhishOne simulates a range of phishing attack types to help you identify areas of weakness in your enterprise security, allowing users to strengthen your enterprise defenses through training.
Product Highlights
- Over 50 phishing email templates on the latest and hottest topics, with free editing capabilities
- End-user personalized training for simulated attacks
- Multi-dimensional data collection for simulated attack drills
- Visual display of risk levels and user performance
- Detailed drill data reports and graphical reports
Pre-defined editable templates
More than 50 popular topics of phishing email attacks can be simulated, and supported custom editing of selected templates.
Training Content Customization Module
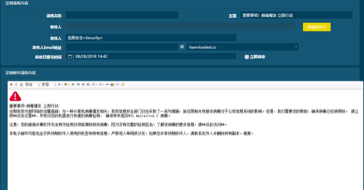
The training content is tailored to meet the customer’s organizational guidelines and concerns, and can be modified and adjusted by the customer at any time.
In-depth reports provide more in-depth information at the enterprise or individual user level, bringing a new understanding of enterprise security.
Multi-dimensional data collection
Not only were the phishing email templates themselves defined with relevant threat types and attack type attributes, but the participants in the simulation exercise were also given certain attributes, and PhishOne captured the following data to provide a valid and comprehensive assessment for the client organization.
- Participants check the timestamp of simulated attack emails
- Where the participants are located
- Length of time participants have been in the training
- Geolocation of participants
- Type of equipment used by the participants
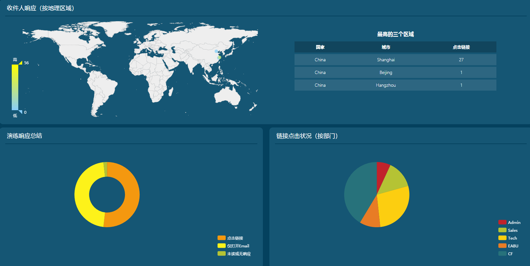
Comprehensive reporting
The report module provides the display and download function of visual reports, and the download function of detailed data tables for each exercise activity is also provided in the exercise list, so that a comprehensive exercise result can be displayed through a series of reports:
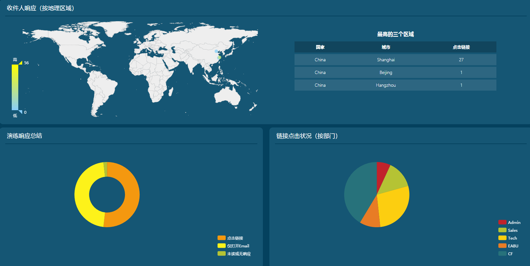
Visual reports show multidimensional data
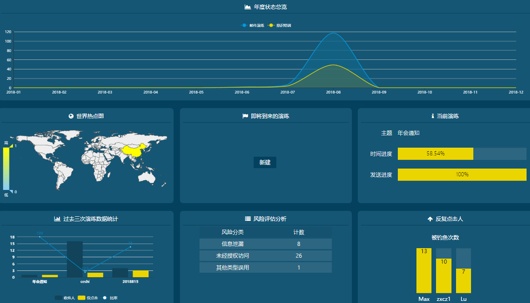
Comprehensive dashboard display
Demonstrate a real return on investment by understanding the security health of your organization with on-demand, intuitive dashboard results The PhishOne dashboard provides an overview of activity results on user vulnerability, allowing you to measure the overall risk level of your entire user group with real-time awareness factor data, including:
- Annual Exercise Overview
- Participant distribution hot zone
- Status of drills to be executed
- Exercise Type Statistics
- Participant Status Statistics
Easily enabled
PhishOne runs entirely in a web browser and is very convenient. To ensure successful delivery of PhishOne emails, simply whitelist the email addresses and domains used in PhishOne campaigns. The list of users is then easily imported via a CSV file. Once the users are uploaded, you are ready to send your first campaign.
Sample Fishing Awareness Simulation Exercise Report.

For more detailed case studies and implementation content, please contact to obtain.:business@cloudfall.cn

