
Ransomware, particularly encrypted ransomware, has quickly become one of the biggest cyber threats to organizations around the world. This criminal business model has been proven to generate significant revenue for cybercriminals, in addition to causing significant operational harm to affected organizations. Yet it is mostly irrelevant to the victim, spanning the globe and affecting all major industry verticals. Small organizations, large enterprises, and even individual home users are all potential targets. For decades, ransomware has existed in a myriad of forms. However, over the past few years, criminals have perfected key components of these attacks, which has led to a proliferation of new malware families, making attack techniques more effective and attracting new malicious players to these lucrative schemes.
Impact
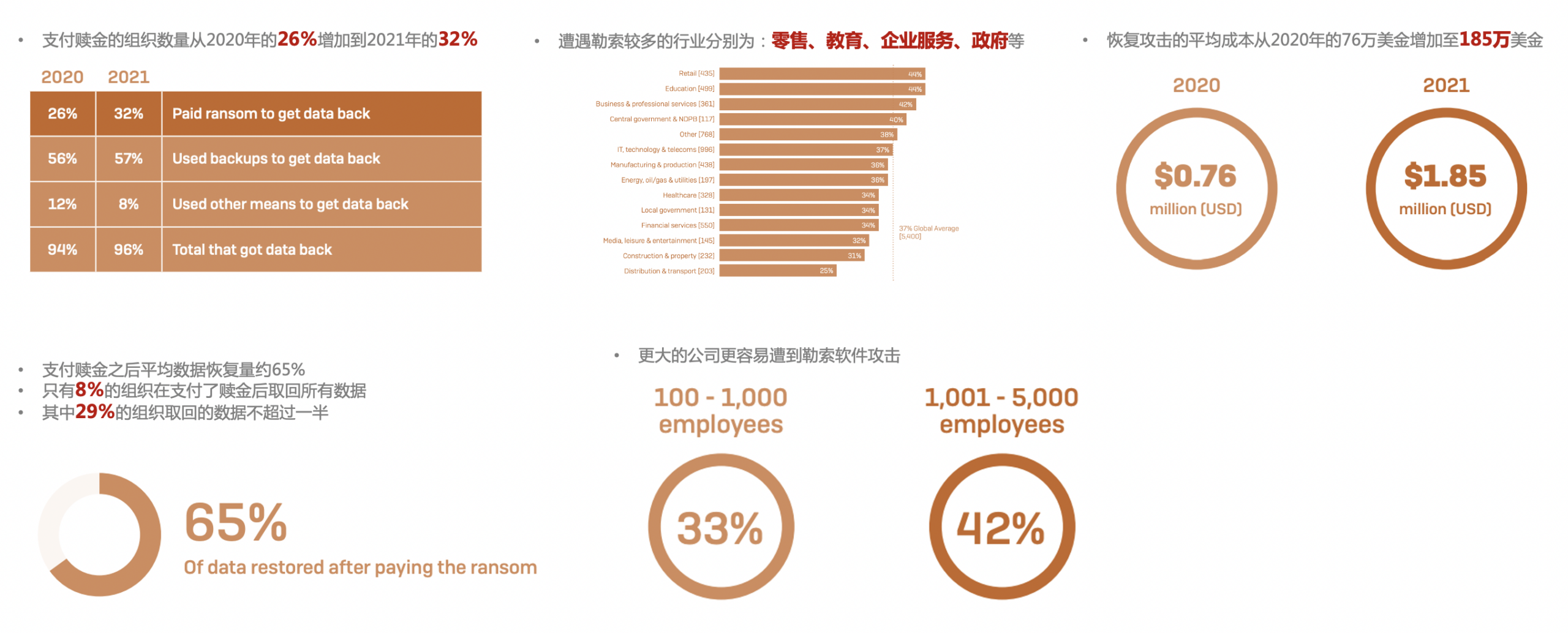
• The financial impact of ransomware is enormous, with estimates varying, but the total cost in the billions of dollars.
• Ransomware is one of the few cybercriminal business models that can use the same attack to harm Fortune 500 companies, the local restaurant down the street, or your grandmother.
• Bitcoin is the enabler for the success of this scheme. The payment methods that ransom payments relied on in the early days have been shut down or forced to be regulated, but bitcoin is not governed by a central authority and there is no law to act on it.
• Initially, the ransom attack was targeted mainly for windows systems. But adversaries have started to expand their targets to other platforms, such as Mac OSX operating system
• Unless organizations around the world adopt a precautionary mindset and stop paying ransoms to get their data back, this criminal scheme will continue to threaten all Internet-connected devices.
Preparation
•Backup and recovery: to facilitate successful data recovery after a ransom attack.
• Network share access control: To stop the spread of ransomware, review the use of network shares to ensure that write access is limited to a minimum number of users and systems.
• Information security awareness education: Ransomware is often triggered by emails and clicks on malicious links, and awareness education for corporate employees should be conducted from time to time to reduce ransomware attacks
Our email phishing simulation platform can help your business improve overall security awareness.
Protection & Detection
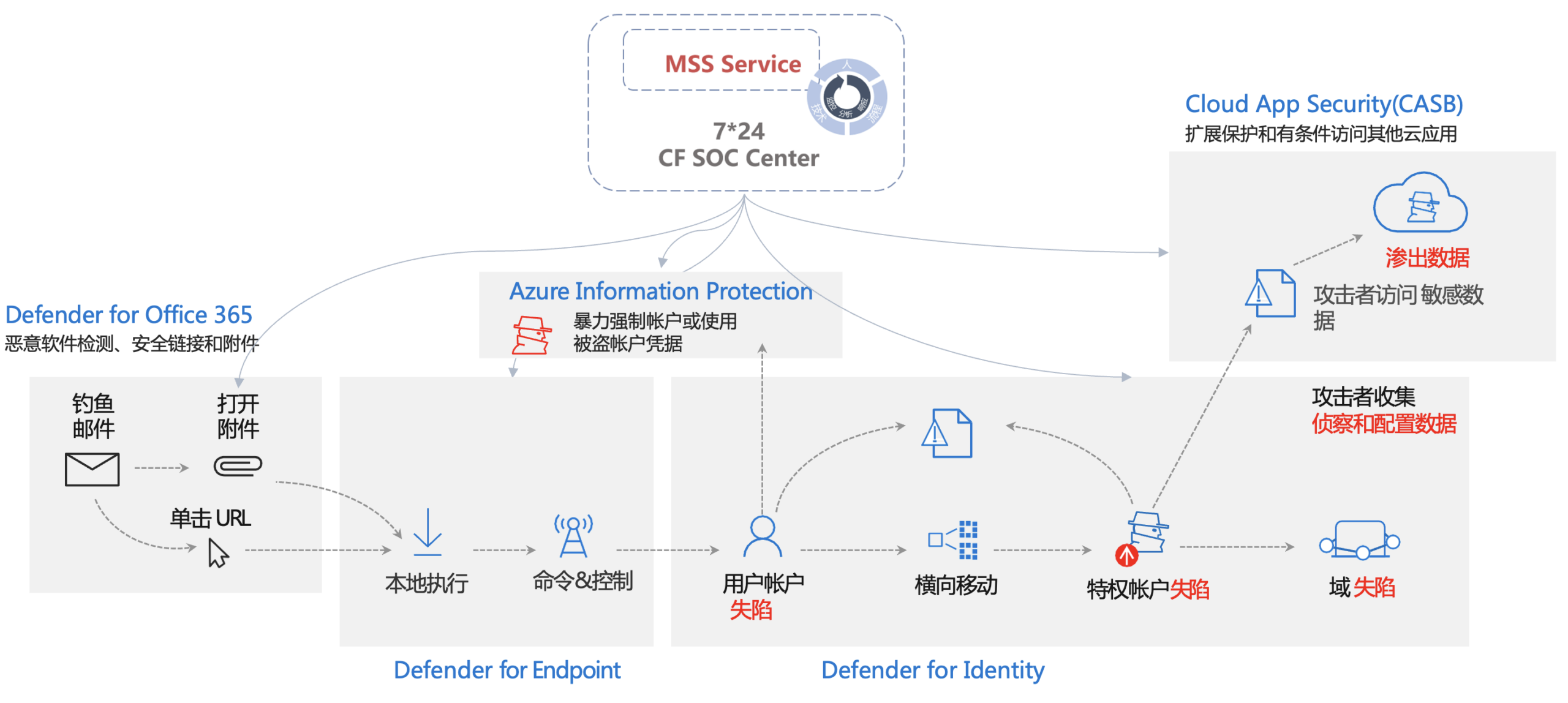
• Email and executable controls: Ransomware typically begins with an email message carrying a Windows® executable file. Network security appliances, such as next-generation firewalls, can identify these files as they traverse the network and can also block or quarantine them.
• Unknown malware prevention: Signature-based detection systems used to detect new malware have proven to be unreliable. Unknown malware prevention systems should be used to enhance network security appliances.
• Endpoint controls: While network-based security devices are sometimes blind to attack events, endpoint-based controls are able to stop the execution of malicious files before they begin.
Our Managed Security Service Series (MSS) can significantly improve network and endpoint defenses, while also providing significant defense against unknown malware:
Response
• Understanding the threat: In some cases, security vendors have found ways to decrypt files without going to the ransom payment. You can find some of the information left behind by the ransom in your system or use an intelligent system to identify some of the ransom messages.
• Prepare for the worst: Getting your files back by paying a ransom should be a last resort. If you have decided to pay the ransom, you should be prepared to pay in a timely manner.
Our incident response services help organizations minimize risk and loss through a standard classification hierarchy and proven processes for effective security incident response:

