Security in Cloud
Is the public cloud itself secure enough? The answer is also yes.
By design, hyperscale cloud providers invest billions of dollars to protect their data centers, build security services, invest in staff training, locate security incidents and fix them quickly. This all comes with a higher level of investment, attention and expertise than most organizations dedicate to protecting their local data centers.
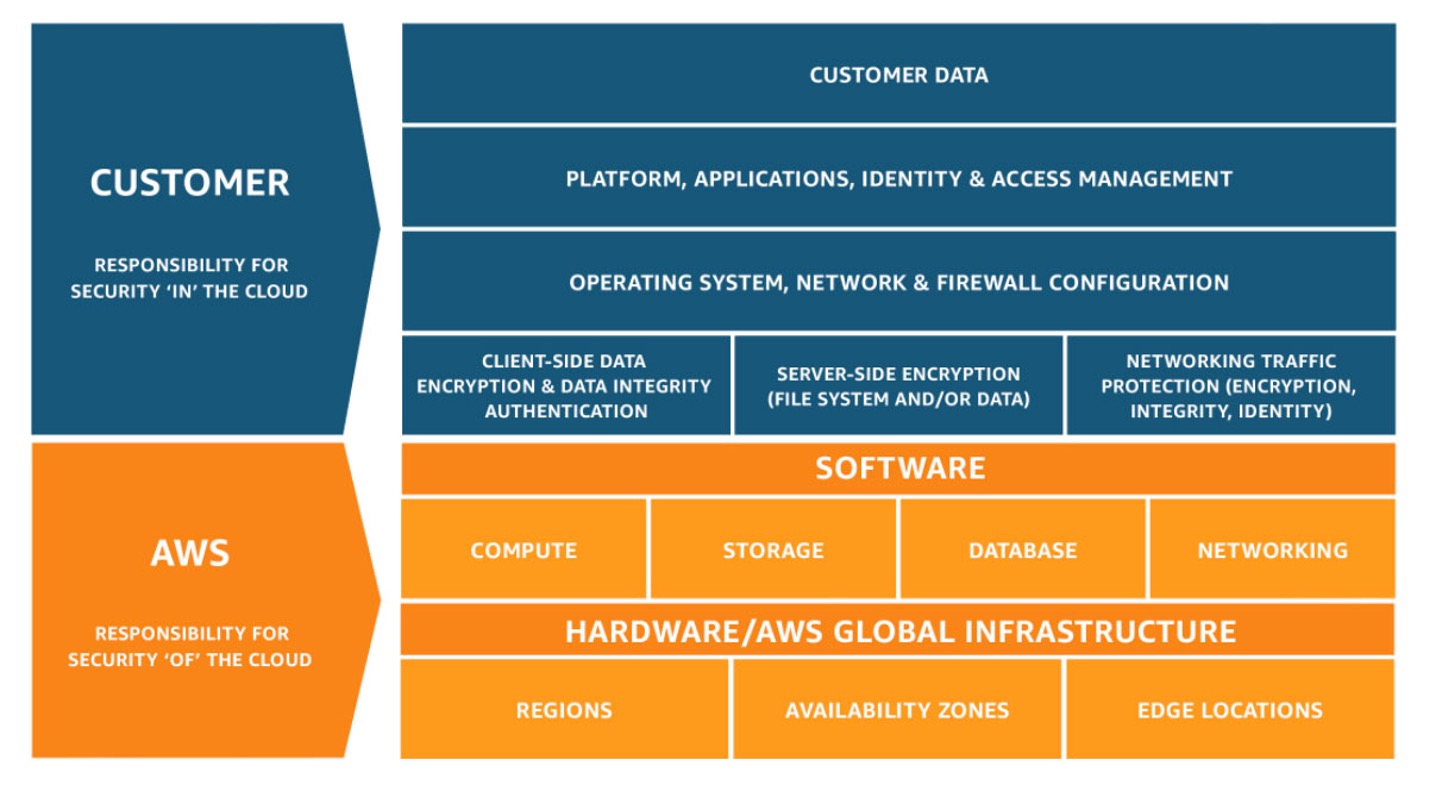
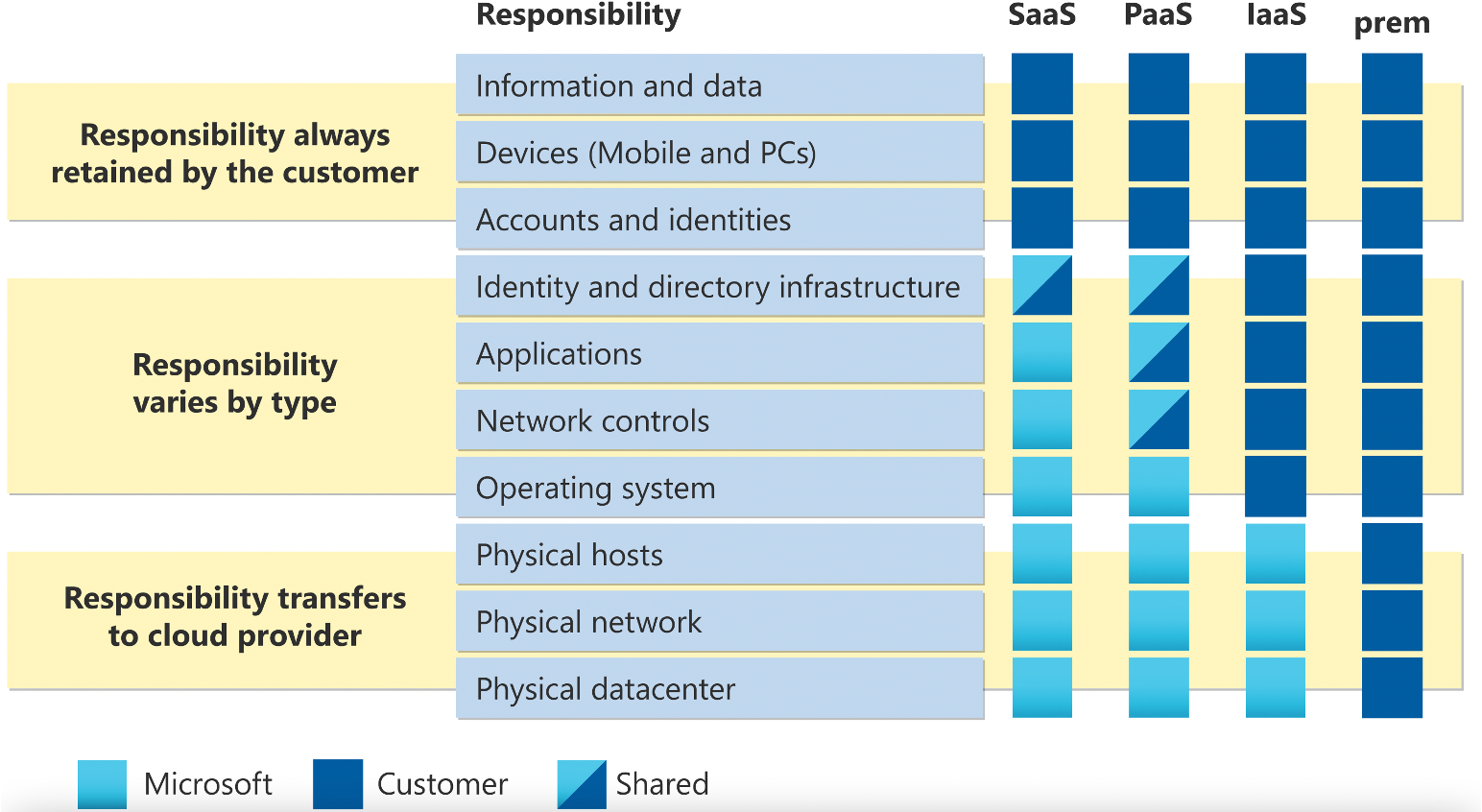
As we gradually accept and understand the security of the public cloud itself, as an enterprise user, the focus comes to the topic of security “in” the public cloud. According to the common responsibility sharing model, we can see that cloud operators are mainly responsible for the security of the cloud itself, while customers will be responsible for the security of the cloud.
Cloud-based Value Returns
When users have a clear understanding of what their organization is doing in terms of business and processes, they can better understand what benefits the organization might gain from a cloud strategy and the costs associated with the migration.
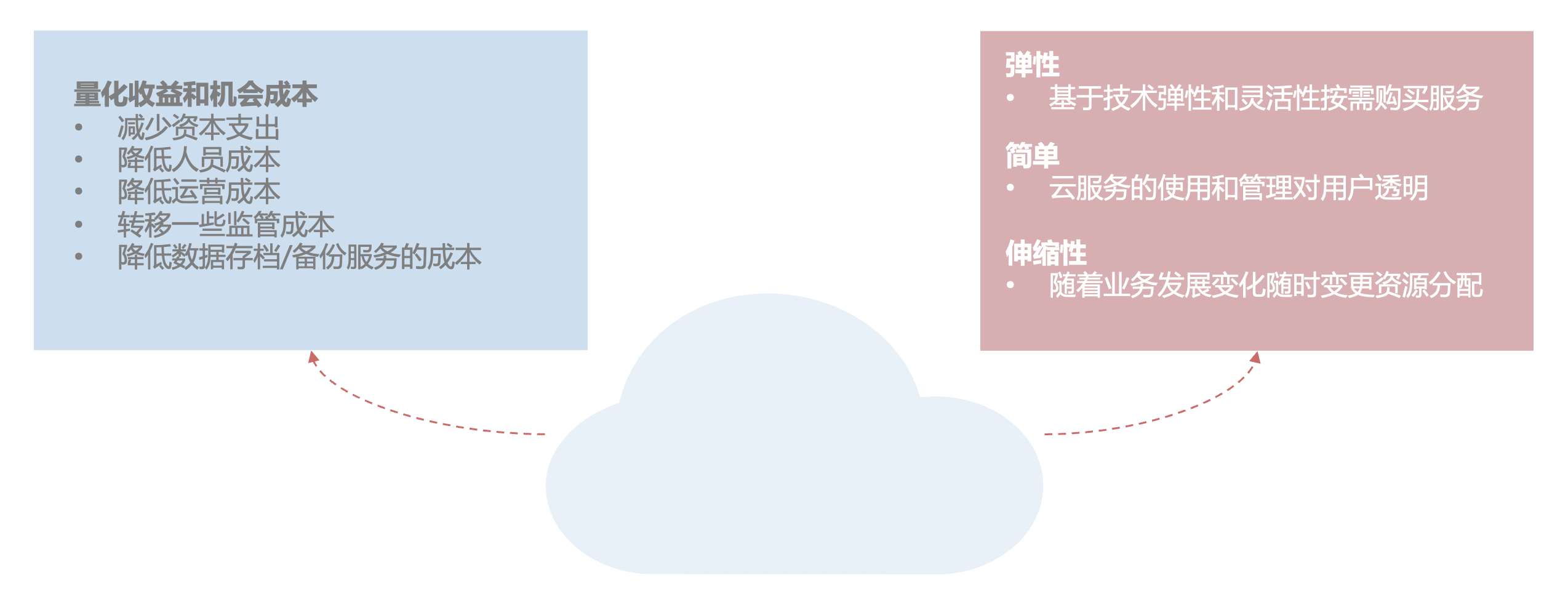
- The biggest driver driving organizations to move to the cloud today is cost savings, which is an important and valid consideration
- The arrival of the cloud and its associated technologies offers many advantages: elasticity, simplicity and scalability, and for information security scenarios, cloud security and cloud-enabled services have all of these same cost-benefit advantages and technical features
For information security scenarios, cloud security and cloud-based services also have all of the above cost-benefit advantages and technical features!
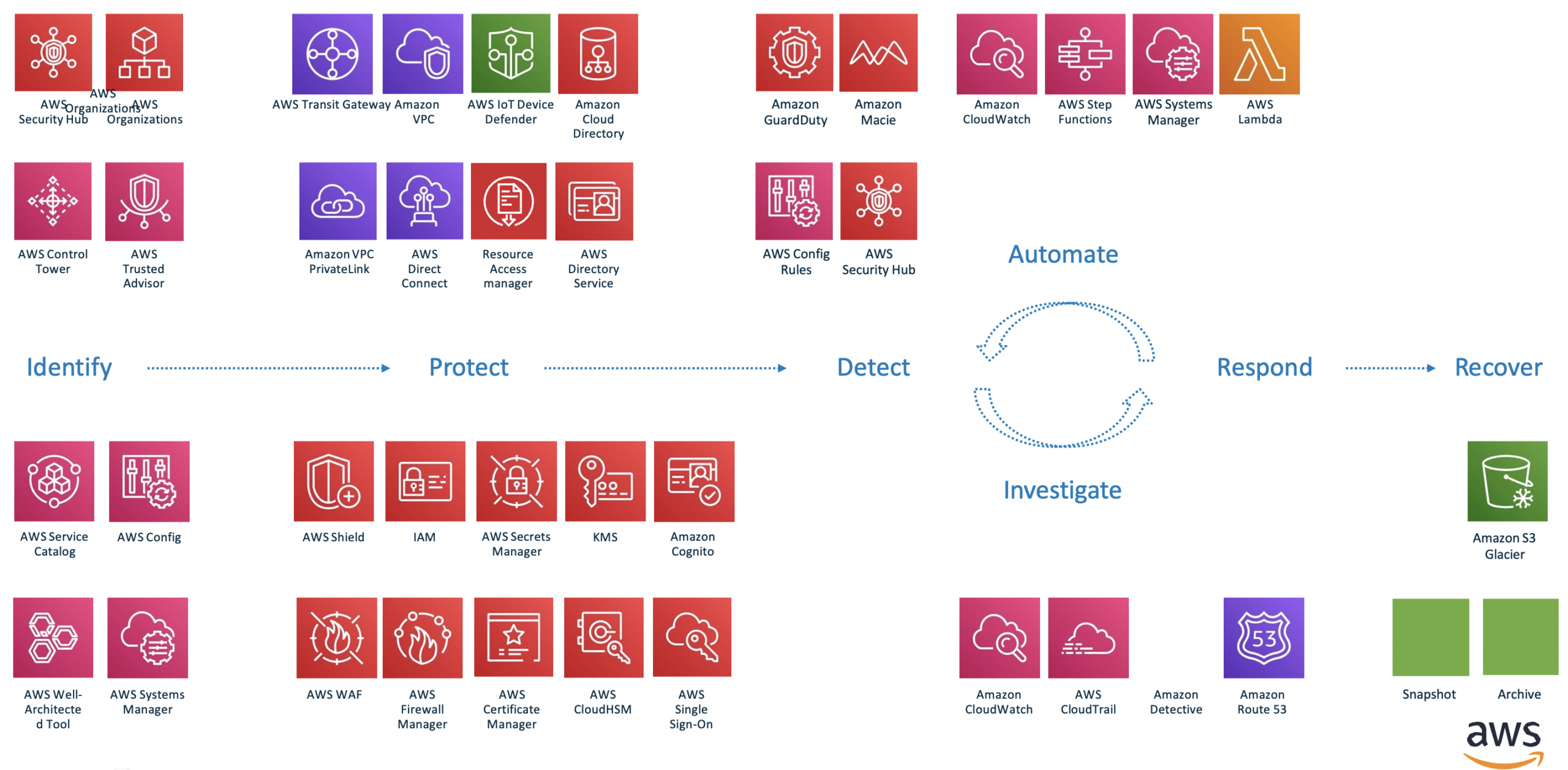
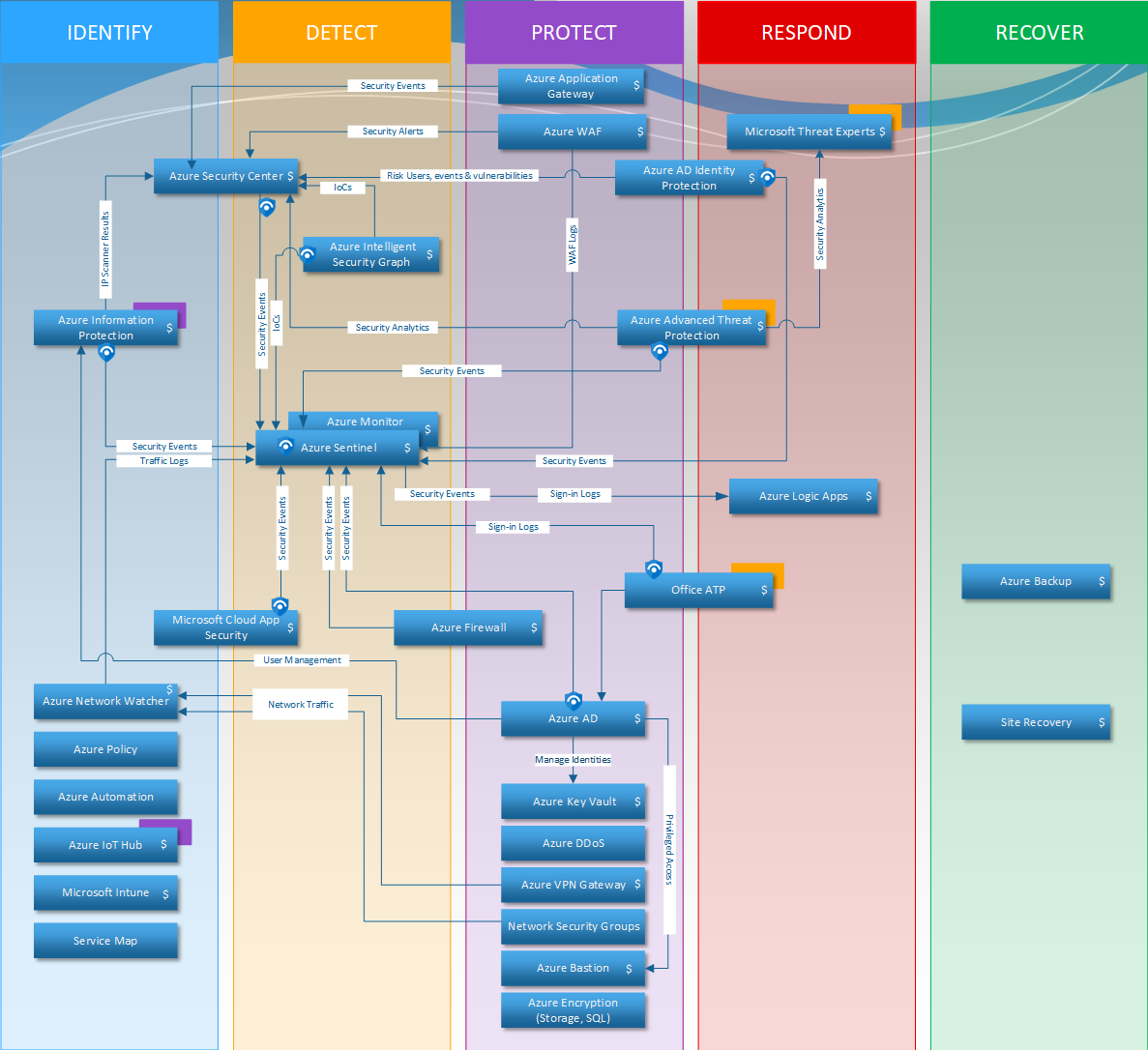
Security Solutions in the Cloud
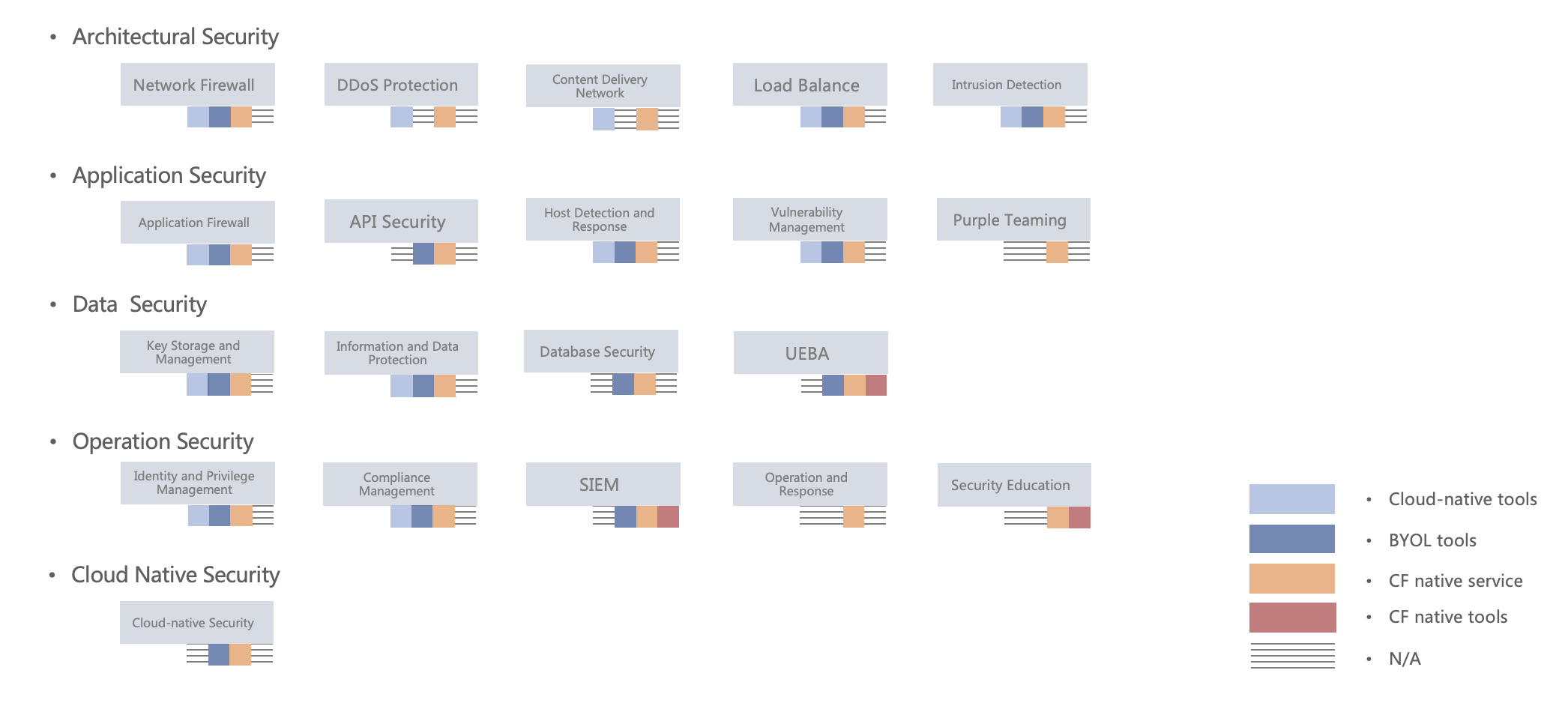
We focus on common security scenarios in the cloud, helping enterprise users design, build and operate security systems on the cloud, including cloud-native security tools and cloud-enabled BYOL tools, and maximize the value of security investments while reducing total cost of ownership (TCO) through a combination of cloud-styled native services and native tools.
We understand and use cloud-native tools, third-party security tools combined with Cloudfall native tools and services to help users improve and operate scenarios related to architecture security, application security, data security, operational security and cloud-native security.
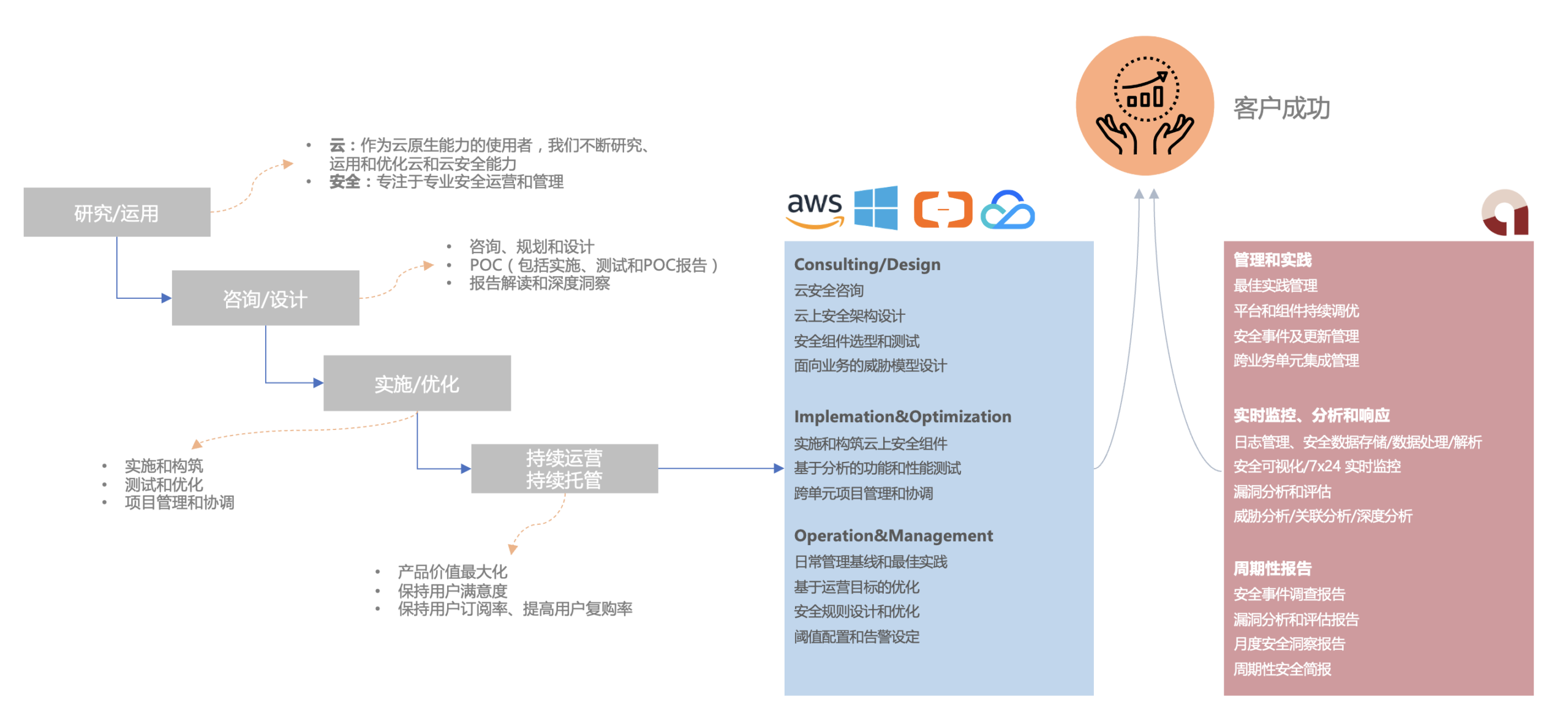
- CLoud:As a user of cloud-native capabilities, we continuously research, apply and optimize cloud and cloud security capabilities
- Security:Focused on professional security operations and management
- Complete Lifecycle:Leveraging our experience and practice in all aspects of the cloud and security lifecycle to help users succeed in their businesses
Mainstream carrier counterpart
- Maximize the value of cloud-native security according to the characteristics and capabilities of different cloud operators
- With reference to the international mainstream security framework (such as CSF/ATT&CK, etc.) to help customers plan the security construction “blueprint”, and through an effective security operation system to help the enterprise security architecture continue to effectively and continuously improve the continuous progression…