SOC-as-a-Service
A Subscription-based Service
Cloudfall provides a full set of fully managed security operation center services to help enterprises monitor, analyze and respond to security incidents and issues through a unified and centralized SOC center by building its own IP security monitoring and analysis platform (InsightX platform). This one combines people, process, technology and data to help customers achieve comprehensive security. At the same time, either on-premises or public cloud VPC, IX on-demand deployment or IXCloud approach provides flexibility to achieve security operation requirements.
Implementing a tiered progression through a unified and centralized service cloud approach.
Establishing strong ties with diverse security vendors to optimize security investment value.
Continuous real-time (24/7) monitoring, analysis, and response.
Maximizing the value of security investments.
Security operations can be progressive
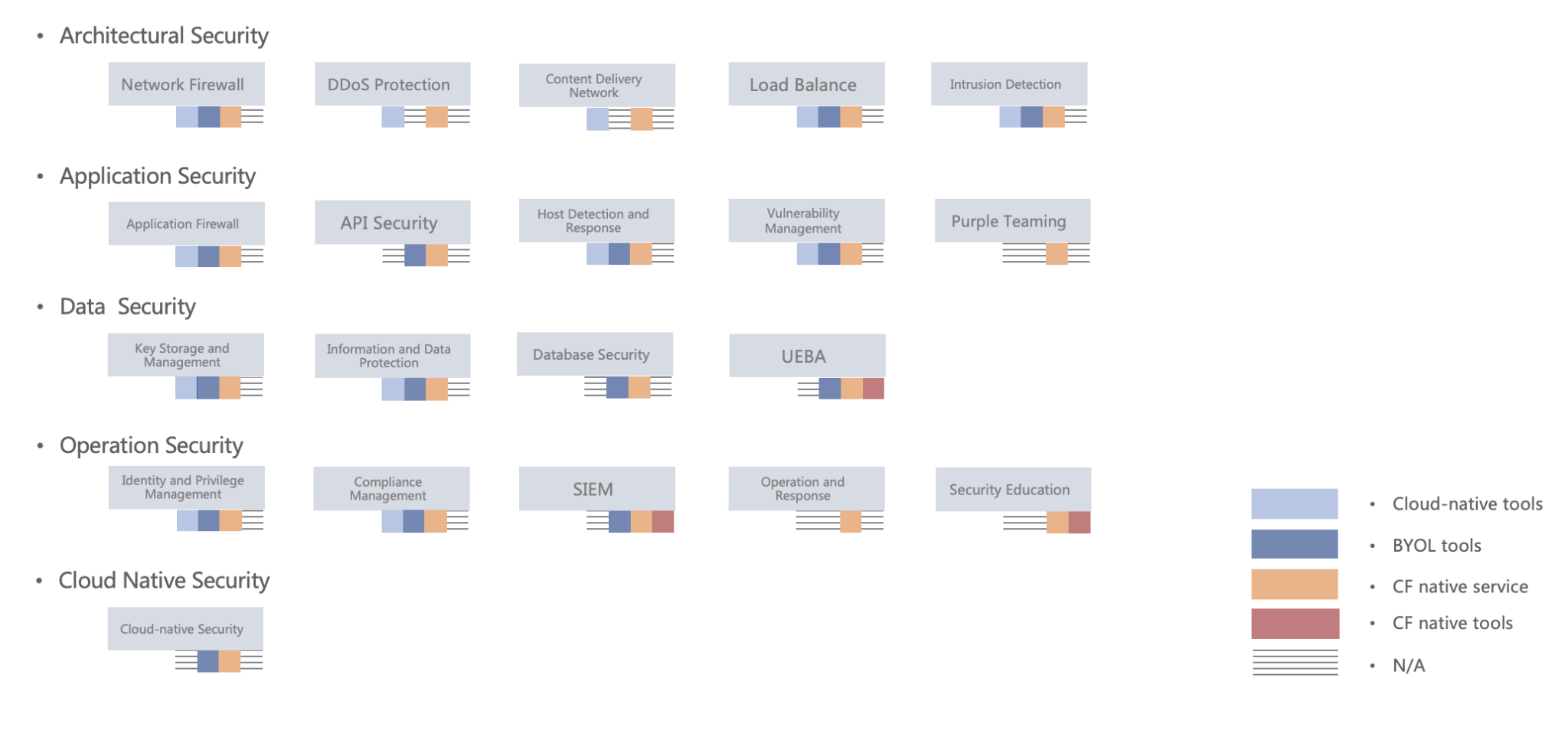
To address the security operation pain points of medium-sized enterprises, we continue to decompose the “SOC-as-a-Service” in layers and modularize the output, trying to change the traditional SOC “big and comprehensive” and also “heavy”
stereotype. We try to change the stereotype that traditional SOCs are “big and comprehensive” and “heavy” at the same time. For the common security management and operation status of medium-sized and small enterprises, the modular
subscription service approach can be delivered more flexibly to find a sustainable security progression in the balance of business and security.
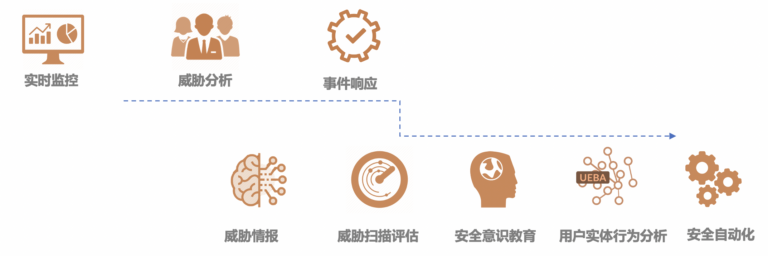
Different modules of security operation services correspond to the security requirements of medium-sized enterprises at different stages, while following the complete professional SOC expansion architecture and system, which can be seamlessly expanded in phases.
Security operation can be started in small ways
In security operations, the more extensive and comprehensive the collection of security log data, the more accurate and real-time the analysis and presentation of results should be. However, when a massive amount of log data is collected, a significant volume of irrelevant and invalid data “noise” also generates numerous false positives, obscuring the threat information that users are genuinely concerned about. Objectively, medium-sized enterprises lack professional security personnel and skills, making it difficult to analyze and process large volumes of logs.
Many medium-sized enterprises purchase expensive and specialized security products, yet they lack the manpower to efficiently analyze these products, leading to the possibility of important security events and information being overlooked. Additionally, these different security products operate in isolation, lacking correlation and the ability to search for clues and rules across different logs.
Minimizing the scope of service targets
Focusing on one or a few sets of security systems
Advanced analytical capabilities
Achieving operations with minimal manpower and resources
High cost-effectiveness in security operations
Enable rapid deployment for small and medium-sized enterprises
Reducing overall threat risks
Quickly reducing overall threat risks for enterprises